自分的には凄く良く眠れる。睡眠薬だと依存性とか、翌日まで眠気があるとか聞くから、なかなか手が出しにくいんだよね。サプリならそんな心配いらないし、効き目も実感してるから気に入ってる。

左記クレジットカード、銀行振込、コンビニ決済に対応



更新日:2025/6/9
| 商品名 | フルナイト | ハイプロン | ハイプナイト | ソクナイト | アモバン・ジェネリック | メラトニン(NOW Foods) | バスピン | APOゾピクロン | タガラ | メラトニンプラス5HTPアドバンスト |
|---|---|---|---|---|---|---|---|---|---|---|
| 商品画像 |  |  |  |  |  |  |  |  |  | |
| 特徴1 | スムーズに入眠できる超短時間型の睡眠薬 | すみやかに入眠できる超短時間型 | 実績ある睡眠薬ルネスタのジェネリック | 超短時間(2~4時間)のみ効果を発揮 | 入眠障害に効くアモバンのジェネリック | 自然な入眠が期待できる「快眠サプリ」 | 依存しにくい抗不安薬 | ・夜なかなか眠れない方におすすめの睡眠薬 | ・天然成分で安全性が高いハーブ | ・疲労回復や集中力の向上にも効果的 |
| 特徴2 | 作用時間が短く、翌朝に眠気が残りにくい | 寝覚めがよく眠気を引きずらない | 依存性が比較的低い有効成分を配合 | ふらつきや転倒などが起きにくい | 翌朝に眠気を引きずらない | 製造元は老舗サプリメーカーの「NOW Foods」 | 穏やかに効いて副作用が少ない | ・即効性が高く、依存性も低い | ・体に負担をかけずに不眠症を整えられる | ・メラトニンの健康効果にも期待できる |
| 内容量 | 2mgx50錠 | 10mgx100錠 | 1mgx50錠 | 2mg50錠x1箱 | 7.5mgx30錠 | 3mg60錠x1本 | 5mgx200錠 | 7.5mgx30錠 | 60錠 | 60錠 |
| 価格 | 4,110円 | 4,590円 | 3,000円 | 4,110円 | 2,400円 | 4,160円 | 5,400円 | 3,100円 | 1,700円 | 4,460円 |

| 個数 | 販売価格(1錠あたり) | 販売価格(箱) | ポイント | 購入 |
|---|---|---|---|---|
| 100錠 | 35円 | 3,560円 | 106pt | 売り切れ |
| 200錠 | 29円 | 5,840円 | 175pt | 売り切れ |
| 300錠 | 23円 | 7,130円 | 213pt | 売り切れ |






①1万円以上で送料無料
1回の注文で10,000円以上だった場合、1,000円の送料が無料となります。
まとめ買いをすると1商品あたりのコストパフォーマンスが高くなるためおすすめです。
②プライバシー守る安心梱包
外箱に当サイト名や商品名が記載されることはないため、ご家族や配達員など第三者に内容を知られることは御座いません。

③100%メーカー正規品取り扱い
当サイトの商品は100%メーカー正規品となっており、第三者機関による鑑定も行っております。
商品の破損などがあった場合は再配送などにて対応させて頂きますので、ご連絡頂ければ幸いです。

④いつでも購入可能 処方箋不要
サイト上では24時間いつでもご注文を受けております。
また、お電話によるご注文も受け付けておりますのでネットが苦手な方はお気軽にどうぞ。

⑤商品到着100%
商品発送後はお荷物の追跡状況が分かる追跡番号をご案内させて頂きます。
郵便局には保管期限がありますのでご注意ください。
・自宅配達で不在だった場合の保管期限・・・16日間前後
・郵便局留めとした場合の保管期限・・・7~30日間

⑥コンビニ決済利用可能
ご近所のコンビニにていつでもお支払可能です。
セブンイレブンに限り店舗での機械操作を必要とせず、手続き完了後に表示されるバーコードや払込票番号をレジに提示することでお支払い頂けます。

メラトニンタイムリリース 5mg x 300錠
7,130円
ポイント:213pt
10,000円以上購入で送料無料
売り切れ

| 型 | 超短時間型 | 短時間型 | 中間型 | 長時間型 |
|---|---|---|---|---|
| 代表的な商品名 | ルネスタ | レンドルミン | ユーロジン | ドラール |
| 効果のピーク時間 | 1時間前後 | 1~3時間 | 1~3時間 | 3~5時間 |
| 効果時間 | 2~4時間 | 6~10時間 | 20~24時間 | 24時間以上 |
| 向いている人 | 寝付きが悪い | 寝付きが悪い 夜中に何度も目が 覚める | 夜中に何度も 目が覚める | 予定よりも早く 目が覚める |
自分的には凄く良く眠れる。睡眠薬だと依存性とか、翌日まで眠気があるとか聞くから、なかなか手が出しにくいんだよね。サプリならそんな心配いらないし、効き目も実感してるから気に入ってる。
果たして本当に効くのでしょうか。2週間ほど飲み続けていますが、自然と眠気が襲ってくる気配がありません。このまま続けるか迷いますね。
| 1日の服用回数 | 1回 |
|---|---|
| 1日の服用量 | 1錠 |
| 服用のタイミング | 就寝の20分前 |
| 服用間隔 | 24時間以上 |
本製品は海外製のため、期限表記が日本と異なる場合がございます。
パッケージ裏面や側面、シートなどに以下のような表記がされています。
| EXP | 使用期限 例:EXP 12/2025→2025年12月まで使用可 |
|---|---|
| MFG または MFD | 製造日 例:MFG 03/2023 |
| BEST BEFORE | 品質が最も安定している目安日 |
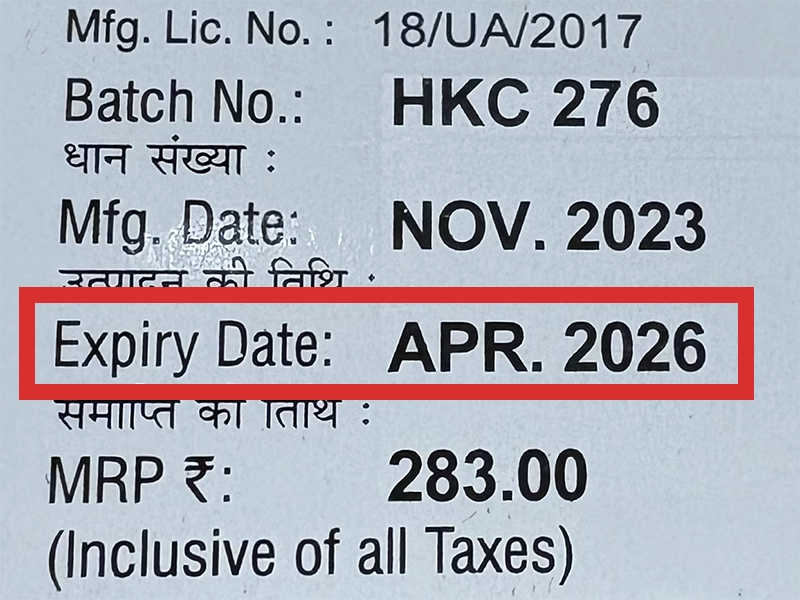
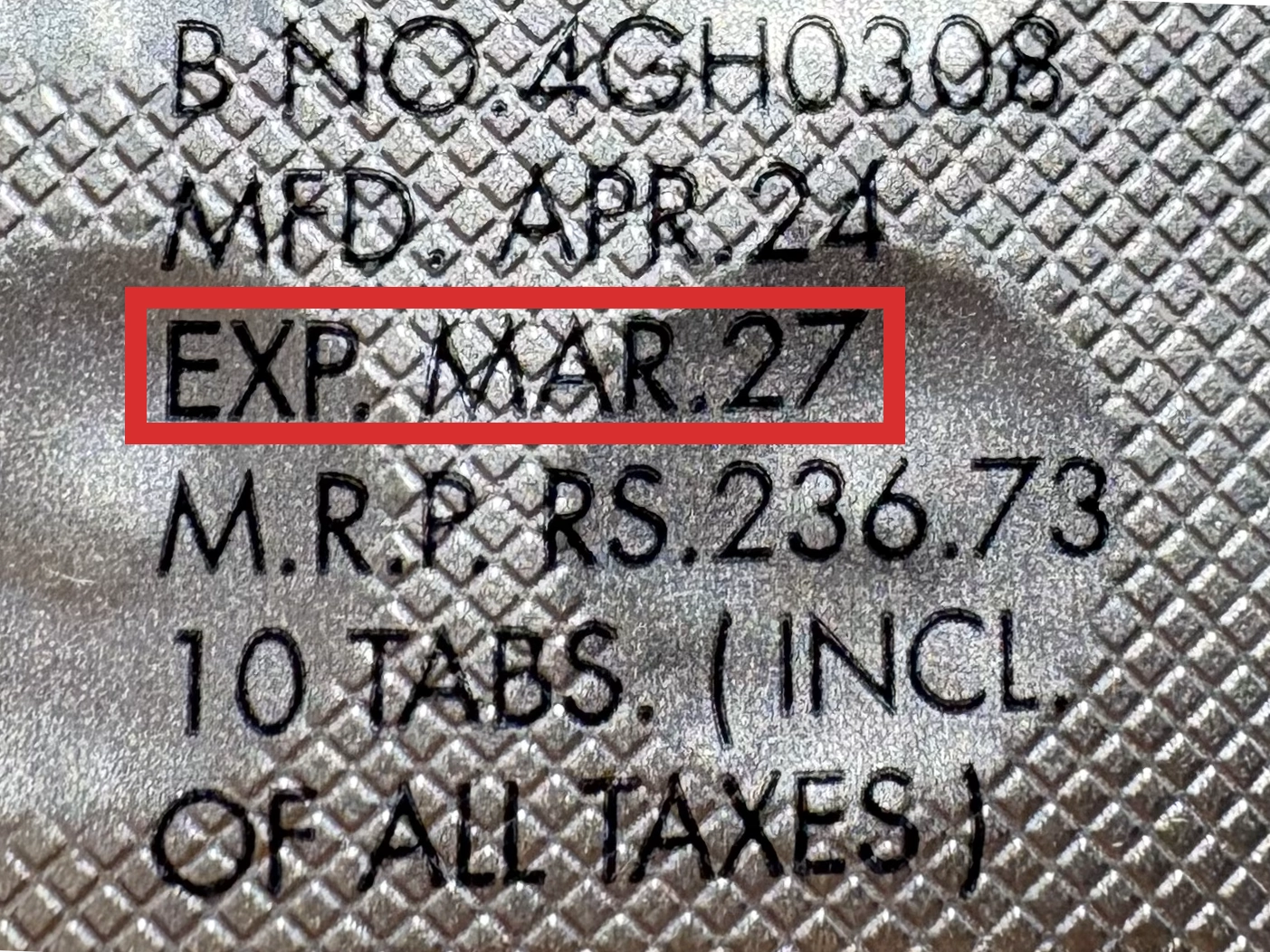
※国や製品により日付の並び(例:月/年、日/月/年)が異なる場合がありますのでご注意ください
EXP(Expiry Date) の表記がなく、MFG または MFDしか記載がないケースがあります。
この場合は MFG(MFD) から2~3年が使用期限の目安です。
※「LOT」や「BATCH」の表記は製造番号であり期限ではありません。

パッケージ例となります。
商品やご注文単位によってはシート単位でのお届けとなる場合が御座います。
外箱に当サイト名や商品名が記載されることはないため、ご家族や配達員など第三者に内容を知られることは御座いません。
睡眠薬よりも飲みやすいし、依存性の心配がない。効果が出てくるまでは相当時間がかかる。なんともいえないといった使い心地。継続するかどうか、現在検討中。ご参考までに。
長年、不眠症に悩み続けている者です。さまざまな睡眠サプリを試してきましたが、これは比較的効果を感じられました!国内の睡眠サプリよりも効き目があるのは確かなので、睡眠の悩みがある人は試す価値があるかと。
海外旅行から戻ってきて、時差ボケがヤバいときの対策用に購入させてもらいました。案の定これのお世話になっていますが、だいぶゆっくり寝れるようになってきました。効き目が出てくるまでもう少し早かったら、もっと嬉しかったです。
自分的には凄く良く眠れる。睡眠薬だと依存性とか、翌日まで眠気があるとか聞くから、なかなか手が出しにくいんだよね。サプリならそんな心配いらないし、効き目も実感してるから気に入ってる。
果たして本当に効くのでしょうか。2週間ほど飲み続けていますが、自然と眠気が襲ってくる気配がありません。このまま続けるか迷いますね。
商品口コミの投稿は会員のみ行えるようになっております。
お手数ですが会員ログインの上でご投稿頂きますようお願いいたします。
口コミをご投稿頂いたお客様にはポイントをプレゼントさせて頂いております。
文章のみであれば100ポイント、文章+写真付きのものは300ポイントをプレゼントさせて頂きます。
規約や詳細などはこちらをご確認くださいませ。